Anti-black hand file verification is enough
I do not know if you noticed that although Thunder and other download software can automatically verify the download data, but some software download page (such as the Windows installation package download page), in addition to the software download link, but also give such as MD5, SHA1, CRC32 file check code data. So, what additional validation data is available? As an average user, how do we use this data?
File verification often refers to the process of verifying the consistency of a file on a website and a file after downloading using one or more checksums such as MD5, SHA1, CRC32 values, and the like. The check code is generally composed of a string of several lengths. These check codes composed of strings are calculated by the verification program from the contents of the file. Therefore, as long as the content of the file is fixed, the checksum will naturally be a fixed string. In the same way, if the file is modified, or there is a packet loss or error during the download and transmission, the verification code of the downloaded or received file will naturally change. For example: Microsoft's website gives the Windows 10 trial version of the ISO check code, and a system site also provides Microsoft's version of the system ISO download, but we are worried about whether this site provides Microsoft original ISO, then you can use to download to The ISO generated checksums are checked against the checksums provided by Microsoft. If they match, the downloaded ISOs are the original ones. Below we describe several practical methods for generating and verifying file verification data.
Right-click property view
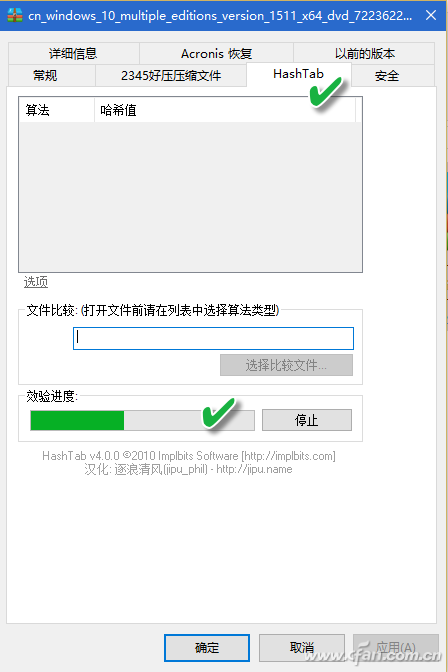
If you often need to verify the file, you can install the checksum program HashTab 4.0 for Windows. After installation, the property verification function will be integrated into the file properties menu window. When you right-click a file and select "Properties", a HashTab tab will be added to the properties window and the progress of verifying the file will be displayed. Bar (Figure 1); According to the length of the file, after waiting at different times, three different check values ​​are displayed in the algorithm and hash list window (Figure 2).
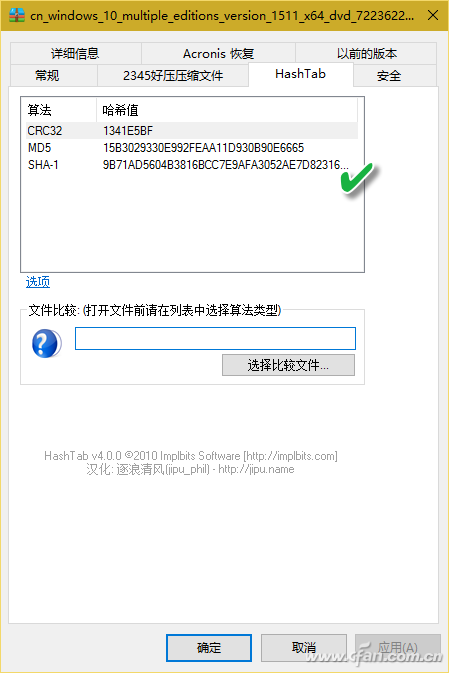
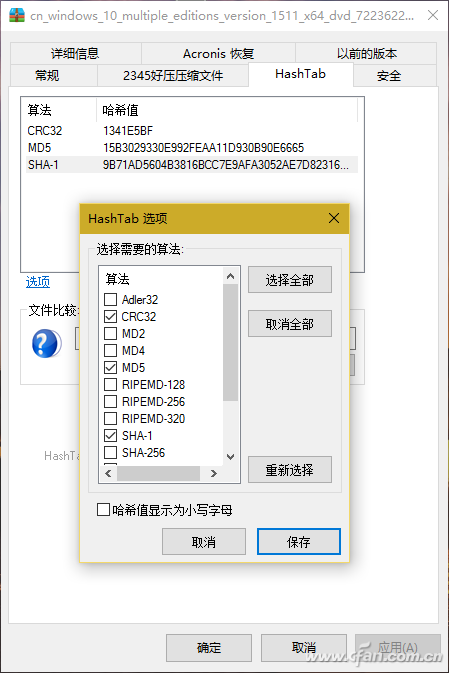
Although the algorithm that the file checker displays by default is only the three types shown in the figure, in fact, the check algorithm included in the software is not limited to these three types. By right-clicking on the list of hash values ​​and selecting the Enter Options window, you can choose from more than a dozen other algorithms (Figure 3).
hint:
If you want to give the check value before the file is online, you can use this method to generate the check code and paste it on the Internet. Similarly, after the file is downloaded, this method can also be used to obtain the check code. Compared with the check code given on the Internet, the consistency of the file content can be known.
Drag to calculate attribute method
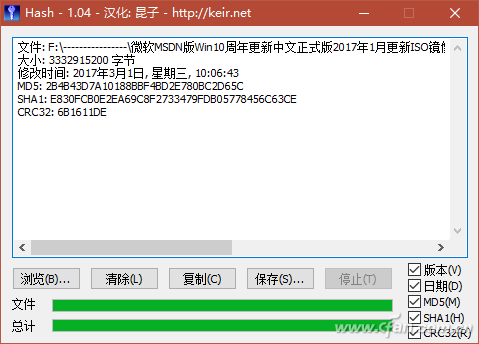
If you do not use file verification often, there is no need to add plug-ins to the file right-click attributes to increase the burden. Just use a green check software Hash_V1.04, drag the file to be verified to the software window, and automatically generate MD5, SHA1, and CRC32 checksums (Figure 4). After verification, the check value can be conveniently saved by using the "copy" and "save" buttons.
In addition, another similar software, Hash Verification Tool V1.4.2, is used to generate a more sophisticated SHA256 check in addition to the above three test values. With this software, multiple files or folders can be dragged and dropped into the window at one time for verification. At the same time, hash value strings can be searched. If there are many files for verification at one time, this function can be used to quickly find the corresponding file. The checksum or a check code corresponds to the file (Figure 5).
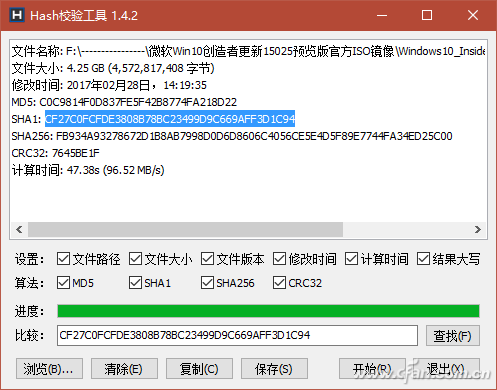
hint:
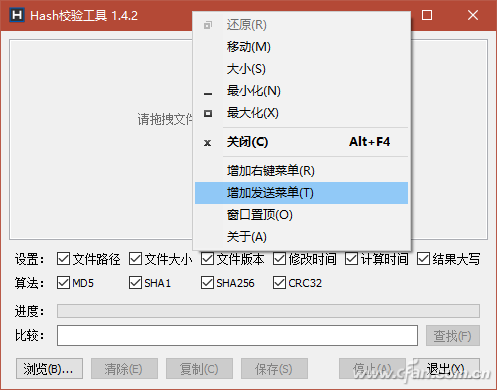
Hash verification tool V1.4.2 version hidden in the add "right-click menu", "send menu", "window sticking top" and other functions, can achieve more convenient operation. Simply right-click on the software title bar and select it from the pop-up menu (Figure 6).
3. Use PowerShell to verify the file
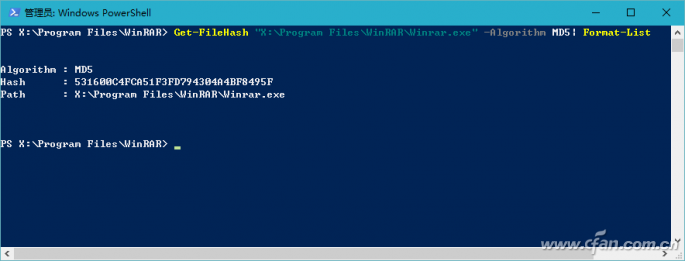
In Windows 10, file verification can also be performed via PowerShell window commands. PowerShell's default command line "Get-FileHash File Path | Format-List" gives the file's SHA256 checksum. If you use the "Get-FileHash File Path-Algorithm Verify Content | Format-List" command to replace "authentication content" with SHA1, MD5 and other forms, you can give the corresponding type of checksum (Figure 7). Note that the space in the file path requires half-width quotation marks, and PowerShell file verification does not support CRC32.
Extended reading: how to deal with "stealing the bullet"
Although the above file verification can guarantee the absolute consistency of the downloaded file and the online file. However, because others can easily modify the original software and use the check code of the modified software to impersonate the check code of the original software, the user is still likely to be fooled. Therefore, there is an urgent need for a verification method that can cope with this crisis. MAC (message check code) came into being. MAC is a string that implements the agreement between the file receiving and sending parties. When the receiving party receives the file, it uses the original file and the agreed MAC string to calculate the HASH value of the file. This calculation is performed after the receiving party obtains the file. The third party cannot intercept the MAC. Only the content of the file cannot calculate the correct HASH value. Therefore, the originality of the file is guaranteed and the fraud is eliminated.
Surface Mount Box,blank surface mount box,electrical mounting box,surface mount electrical box
NINGBO UONICORE ELECTRONICS CO., LTD , https://www.uonicore.com
