Detailed explanation of the design and implementation process of the human-sensing system built with embedded technology
With the rapid economic development, a variety of monitoring equipment has been seen everywhere, playing an important role in different fields. However, in places such as secret rooms, vaults, and warehouses that are related to the safety of major assets, simple video surveillance functions cannot meet their requirements on the security level. The method commonly used in practical applications is: After an abnormal situation occurs, the alarm is sent through an alarm, and the scene situation is recorded through the monitoring equipment for the police to collect evidence during subsequent investigations. Therefore, the real-time performance is extremely poor, and due to the limitation of the physical performance of the front-end detection device of the alarm, it is often affected by environmental factors such as temperature, humidity, and illumination angle, and misjudges the status of the monitoring site, causing false alarms. Happening. At the same time, the continuous long-term work of monitoring equipment is also a waste of energy, which does not conform to the current concept of energy saving and environmental protection. How to reduce the misjudgment rate and reasonably control the working mode of monitoring equipment has become an important research topic in the next stage of development of security equipment used in such special places.
The embedded human sensing system studied in this paper is the security equipment used in such special environments. This system is designed to make accurate and complete judgments and fast and efficient processing of the monitoring site conditions, and better realize the function of security.
Considering that this system is an improvement and expansion of the existing monitoring equipment functions, it needs to be simple and powerful, low overhead, flexible and convenient to use, and at the same time, it should be easy to replace when the parts are damaged, but also beautiful and practical. From a technical point of view , Using embedded technology is the most convenient and reasonable way.
1 System scheme designWith the development of chip technology, a single chip has stronger processing capabilities, making it possible to integrate multiple interfaces. At the same time, due to the increased requirements for reliability, cost, and replacement of various products, embedded systems gradually stand out from the competition of similar products and become the new focus of the IT industry.
Embedded systems are generally recognized as a type of microcomputer system that is application-centric, based on computer technology, software and hardware can be tailored, and meets strict requirements on system functions, reliability, volume, power consumption, and cost. Although the embedded system is in the mainstream position in the architecture, the development process such as Linux, OSGi or Java are all open programming environments, there is no market monopoly, and full of innovation and continuous development. Embedded technology has become the common development direction of communication products and consumer electronics, and has begun to be gradually used in the security field. At the same time, due to the extensive attention of the industry, the development of various embedded processors (hardware) and embedded operating systems (software) has also promoted the progress of embedded technology and the development of networked, digitalized, and intelligent information technology.
In view of the fact that the embedded technology can realize the functions of efficient information collection and data processing, while taking on high requirements and heavy load, the performance is stable and excellent, so this article adopts embedded technology in the design and implementation of the human sensor system.
According to the requirements of various security systems for the accuracy and real-time of information processing, the human-sensing system adopts the following design ideas: the combination of the main chip, image acquisition module and PIR infrared sensor module is used, and the PIR infrared sensor module monitors the scene When an abnormal situation occurs, the main chip is notified to control the image acquisition module to perform periodic image acquisition, and the collected images are processed and recognized. According to the discrimination result, the main chip performs subsequent operations. If there are no abnormal images in the image acquisition module for 10 consecutive cycles, the image acquisition module is closed; otherwise, the alarm device is activated, and the collected images of the last 20 cycles are compressed and stored in the storage device or transmitted to the terminal device. Through the use of such a dual intelligent identification method, the purpose of reducing possible misjudgments of the monitoring site conditions and reasonable control of the working mode of the monitoring equipment is realized, and the effect of intelligent security is truly achieved.
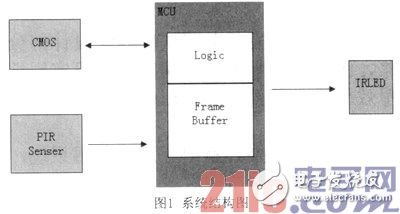
In the picture: PIR Senser (infrared sensor module), which is responsible for physical monitoring of the monitoring site conditions; CMOS "image acquisition module), which completes the image acquisition of the monitoring site conditions; MCU (main chip), which implements system control and image processing. Image recognition and other functions; IRLED (infrared LED supplementary light) auxiliary function module, when the ambient light of the monitoring scene is relatively poor, in order to have a better image collection effect, infrared supplementary light is performed through this module.
2 hardware module structure designBased on the system scheme design in the previous section, the main components of each hardware module of the system are as follows:
2.1 PIR infrared sensor module
The PIR infrared sensor module is always in working condition when it is not powered off. As long as there is a target that meets its trigger conditions in the monitoring range, it will send a high-level signal to notify the main chip to start the image Collect the module, and then perform related operations later. It remains in working condition.
2.2 Image acquisition module
Due to the hardware performance of the image acquisition module, if it works for a long time in the same way as the PIR infrared sensor module, on the one hand, it will consume a lot of power, which does not meet the original intention of energy saving. At the same time, it will also cause great damage to its hardware. Short module life. Therefore, the module adopts the method of starting from the main chip when image acquisition is required. After the module is started, the camera component periodically collects images of the scene in the monitoring range, and saves the collected images to the main chip, and the main chip performs the next step on the image. Before receiving the instruction from the main chip to stop working, it always keeps the state of cyclically executing the above working process.
2.3 Main chip
In addition to the main chip responsible for monitoring the status of the PIR infrared sensor module, controlling the working mode of the image acquisition module, and alarm control operations, there is also a very important task for image processing, image recognition and results of the images collected by the image acquisition module. Judgment, decide whether to perform corresponding alarm control operations. Therefore, the choice of the main chip requires both sufficient memory space and strong processing capabilities. Based on the above requirements, it is finally determined to choose the Samsung S3C6410 ARM7 processing chip as the main chip.
2.4 Infrared LED fill light
The infrared supplement light module is an auxiliary function module of the human sensing system. When the brightness of the picture obtained by the image acquisition module is too low, in order to have a better image acquisition effect, the module performs infrared supplement light when the image acquisition module is working.
Note: In view of the principle of energy saving, the above circuit modules in a long-time working state all use a 3.3-5.0V DC power supply.
3 Software module designIn view of the characteristics of the human-sensing system, the research content of the software module design is mainly the main chip's image acquisition of abnormal conditions in the monitoring field, as well as the subsequent image processing and image recognition algorithms related technologies, excluding image transmission and image compression storage. content.
With the development of monitoring technology, target extraction and effective monitoring have become key technologies in image processing and image recognition. How to accurately extract the actual meaning of the object entity from the image sequence is the basis for the subsequent image recognition of the object entity according to the preset threshold.
3.1 Object extraction
The common methods of object extraction include inter-frame difference method, background difference method and optical flow method. The inter-frame difference method is based on the difference method on time series images, which is not sensitive to external interference and can avoid some unnecessary noise interference, but it is usually difficult to obtain the complete outline of the detection target; optical flow method uses the pixel intensity in the image sequence The time domain change and correlation of each pixel are used to determine the status of the respective pixel positions. Because this method is to confirm the position of each pixel, and the calculation formula is complicated, the calculation amount is relatively large, and it is not suitable for systems with high real-time requirements. in. In view of actual requirements and other factors, the most direct and simple background difference method is used in this design to extract objects from the image obtained by the image acquisition module.
The background difference method needs to store the background image in advance for later use in the difference. Therefore, when the human sensor system is started, the image acquisition module will start to collect and store the image of the current frame, and then the system enters the normal working mode. Since the gray level of the newly-appearing object entity and the gray level of the background will be more obvious, the newly-appearing object entity in the image after the difference will have a larger gray value. The background difference method is based on this principle and extracts the object entity from the background by making a difference between the current image and the background image.
Assuming that the binarized image of the current frame is Ni, the background image is B after binarization, and the image threshold is pt, then the image after the background difference binarization is:
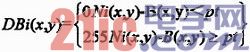
In this way, when the background difference is binarized, the pixels with the gray value of 255 of the image are regarded as the target entity of the object.
3.2 Object recognition
Object recognition is to compare the area of ​​the extracted object entity target point with a preset threshold.
After the object extraction step is completed, an appropriate threshold T needs to be selected according to the actual situation to judge the obtained object entity. When the total area of ​​the connected domain composed of the object entity target points is greater than the threshold T, it is deemed an abnormal situation, and the main chip is notified to activate the alarm device; when the total area of ​​the connected domain composed of the object entity target points is less than the threshold T, it is regarded as PIR The infrared sensor module is triggered by mistake or the object that triggers the PIR infrared sensor module is not an "intruder", it is not an abnormal situation, and there is no need to activate the alarm device.
3.3 Image processing
The background difference method can simply extract the object entity from the background, and can completely obtain the location, size, shape and other information of the object entity. However, due to its own algorithm limitations, this method often encounters noise and changes in the external environment. Impact.
Due to the influence of noise, some points that do not belong to the target entity will be mistakenly classified as target points of the target entity, or due to noise in the background image, some points that originally belong to the target entity will be ignored. In order to reduce the influence of such factors, before the image binarization operation, it is necessary to denoise the image before extracting the object. In addition, due to the influence of environmental factors such as light, shadow pixels with the same visual characteristics as the target entity will appear in the image. If the background difference method is used directly, the total area of ​​the connected domain composed of the target entity target point will be affected by the shadow pixel. The existence of the dots becomes larger, which makes wrong judgments in object recognition. For this reason, before the object is extracted, it is also necessary to perform shadow detection on the current frame in the HSV color space.
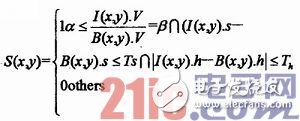
In the formula, I is the current frame, B is the background image, and S is the shadow pixel. Set α as the light source influence coefficient, the stronger the light source, the smaller α; β is to remove the influence of noise. The setting of Ts and Th is to distinguish the difference between the current frame and the background image.
In order to obtain the object entity more accurately, before image recognition, it is necessary to use methods such as mathematical morphology to process the image after the background difference binarization, and set a value when calculating the total area of ​​the connected domain composed of the object entity target points Statistical threshold t, when the area of ​​a connected component is less than t, the area of ​​the connected component is not included in the total area.
At this point, the object entity can be extracted relatively completely, and a more accurate object recognition operation can be performed on this basis.
4 Experimental resultsThis experiment is to verify the feasibility and practical application effect of the object extraction, image processing and image recognition algorithms in the software module design part of the previous section. (Software environment: Linux; size of each frame: 352×288.)
In a closed office, the human-sensing system is activated, and then a person enters and passes through the monitoring area. The human-sensing system accurately determines the target as an "intruder."
The experimental renderings are as follows:

Figure 2 Current frame image

Figure 3 The image obtained by object processing after image processing
Experiments show that the hardware module can operate normally and stably. When connected to the LCD screen to observe the working status of the image acquisition module, the display effect is good. The acquired image is an image of 352&TImes; 288 pixels. Under different brightness conditions, the acquisition is The goals are relatively clear, indicating that the image acquisition module can efficiently complete image acquisition tasks.
The experimental results of the system fully meet the expected design requirements. Based on embedded technology, the human sensing system composed of PIR infrared sensor module, image acquisition module and main chip is stable, reliable and efficient in a security environment.
The image processing, image extraction and object recognition algorithms used can effectively process and recognize the monitored objects, achieving the expected experimental results.
5 ConclusionEconomic development and the advent of the digital information era have created a huge space for the development of embedded technology, and put forward more and higher requirements for the application of monitoring equipment in the security field. Embedded technology is bound to play an important role in the security field, especially in image processing and image recognition.
Based on the development trend and special needs of the security field, this article combines the unique advantages of embedded technology and uses embedded technology to construct a human sensing system with the main chip, image acquisition module and PIR infrared sensor module. The introduction of image processing and image recognition algorithms effectively reduces the misjudgment rate and improves the real-time performance of the system.
The Aluminum Alloy Creative Notebook Stand is stable and durable, stable and does not shake. Laptop Stand Ergonomic bone is supported by an aluminum alloy triangle-shaped stable structure, which has a strong load-bearing capacity and can easily carry 100 g items, and Laptop Stand Holder is stable and not easy to damage.
Shenzhen Chengrong Technology Co.ltd is a high-quality enterprise specializing in metal stamping and CNC production for 12 years. The company mainly aims at the R&D, production and sales of Notebook Laptop Stands and Mobile Phone Stands. From the mold design and processing to machining and product surface oxidation, spraying treatment etc ,integration can fully meet the various processing needs of customers. Have a complete and scientific quality management system, strength and product quality are recognized and trusted by the industry, to meet changing economic and social needs .

Aluminum Alloy Laptop Bracket,Laptop Stand To Keep Cool,Dell Laptop Vertical Stand,Aluminium Alloy Notebook Stand
Shenzhen ChengRong Technology Co.,Ltd. , https://www.laptopstandsupplier.com
