MCU structure and composition, as well as methods and precautions for cracking MCU
First understand what the MCU is - structure and composition
This article can give a lot of reference ideas to students who are interested in MCU protection, but for those who want to be hackers, Zhang Fei is not responsible for the consequences of electronic warfare...
I: CPU, including the operator, controller, and register bank. It is the core component inside the MCU and consists of two parts: the computing component and the control component. The former can complete the arithmetic logic operation of the data, the bit variable processing and the data transfer operation, and the latter is to coordinate the work at a certain timing, and is a component for analyzing and executing the instructions.
II: Memory, including ROM and RAM. ROM program memory, the work of the MCU is executed in a sequence according to the pre-programmed program. The ROM program memory is used to store the programmed program (the system program is compiled and written by the manufacturer). The stored data does not disappear after power down. The ROM is further divided into on-chip memory and off-chip (extended) memory.
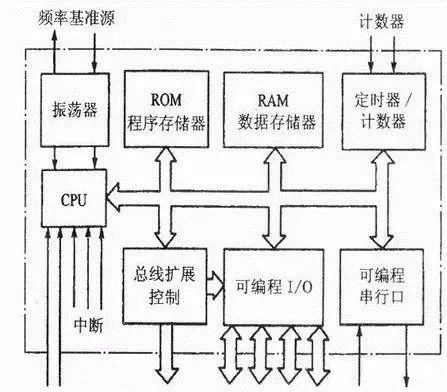
The RAM data memory can write data at any time during the running of the program, and can read the data at any time. Stored data cannot be maintained after power down. RAM is also divided into on-chip data memory and off-chip (extended) memory.
III: Input and output I/O interfaces, connected to external input and output (circuit) devices. Digital I/O interface such as PO/P1/P2/P3, the internal circuit includes circuit such as port latch, output driver and input buffer. Among them, PO is a three-state bidirectional interface, P1/P2/P3 digital I/O port, and the internal driver is an “open collector†output circuit. When applied, internal or external circuits are connected with pull-up resistors. Each port can be used as a digital signal input or output port, and has a multiplexing function (refer to the port function has a first function, a second function or even several functions, which can be flexibly set in the application).
In addition to the digital I/O port, the MCU device also has an ADC analog input and output port. The input signal is converted into a digital (frequency) signal by an internal A/D conversion circuit, and then processed; for an analog signal, After D/A conversion, it is output to an external circuit.
Let me talk about how to crack the MCU method and preventive measures.First, non-intrusive attacks
There is no need to initialize the components. Components can be placed in the test circuit for analysis during attack, or components can be connected separately. Once successful, this type of attack is easy to popularize and there is no significant overhead in re-attacking. In addition, the use of this attack will not leave a trace. Therefore, this is considered to be the biggest threat to the hardware security of any component. At the same time, it usually takes a lot of time and effort to find a non-intrusive attack method for a particular component. This usually reverses the engineering of components, including disassembling software and understanding hardware layouts.
Non-intrusive attacks can be passive or active. Passive attacks, also known as side attacks, do not affect the component being attacked, but usually observe its signal and electromagnetic radiation. Such as power analysis and clock attack. Active attacks, such as exhaustive attacks and noisy attacks, feature adding signals to components, including power lines.
A simple non-intrusive attack can be to replicate an SRAM-based FPGA with a powered configuration. Connect the JATG interface for the configuration chip and capture all signals with an oscilloscope or logic analyzer. You can then analyze the waveform and reply to a unique command.
When only half of the FPGA resources are used, the fact that the data stream can be slightly changed to camouflage piracy can be used. Leave a little space in the configuration without affecting the operation of the components. The JTAG interface also has some freedom in transmitting signal timing, so the pirated waveform can be set to look different from the original signal. In addition, the cracker can exchange the row address when uploading, giving the impression that the design is completely different.
Protection and safety
Semiconductor manufacturers have provided major customers with measures to enhance product anti-cracking capabilities: customer printing on the packaging replaces standard chip models. This gives the impression that the product is designed by a custom integrated circuit. As we all know, ASIC provides good protection measures to prevent multiple attacks, and only a few experienced and well-equipped crackers can successfully crack. This will discourage many potential crackers. But a confident cracker will try to determine if the chip is really an ASIC in a simple way. The easiest way is to look at the pins that are connected to the power, ground, clock, reset, serial or other interface. This result is very reliable compared to suspected microcontrollers in the database, and each microcontroller has its own pin characteristics. Once the similarity is found, put it on the general purpose writer and try to read the result.
Another easy way is to restrict access to the program memory. Usually used in smart cards, but also used in some microcontrollers. This is not a very reliable and practical method. Of course, it is used very well in smart cards, and all customers are forced to sign non-proliferation agreements with chip manufacturers. But microcontrollers are rare, and many microcontrollers that can be programmed by general-purpose programmers are available in the world. Even if there are no programming specifications in the file, you can use the low-cost oscilloscope to take out the required waveforms in a few hours. If the microcontroller is not supported by a special general purpose writer, a direct and complete protocol can still be obtained by purchasing a development board from the manufacturer.
Second, timing attacks (Timing attacks)
Some safety-related operations use input values ​​and keys that are compared by semiconductor chips for different times. Careful timing measurements and analysis can recover the key. This method was first mentioned in the 1996 literature. Later, this attack successfully cracked the actual RSA-signed smart card.
In order for the attack to succeed, information about the device needs to be collected, compared to the processing time integration, such as question-answer delay. Many cryptographic algorithms are susceptible to timing attacks, the main reason being software to execute algorithms. That includes performing branches and operating conditions that are needed to skip at the right time; using caching; not fixing time processing instructions such as multipliers and crossovers; and a host of other reasons. The result is that execution capabilities typically depend on the key and the input data.

Blind signatures can be used to prevent such attacks. This method uses a combination of selected random numbers and input data to prevent the cracker from knowing the mathematical algorithm of the input data.
Timing attacks can be used in security-protected password-based microcontrollers, or systems that use a definite digital card or password for access control, such as Dallas' iButton products. A common risk in these systems is that the consecutive numbers entered are verified again in the database. The system needs to constantly check each byte of the key entered into the database. Once an incorrect byte is found, it stops immediately and then switches to the next one until the last one. Therefore, the cracker can easily measure the time when the last key is input to request another one, and the similarity of the found key is obtained. Try a relatively small number and it is possible to find a matching key.
To prevent these attacks, designers need to carefully calculate the processor's cycle. The correct and incorrect time is the same when the passwords are compared. For example, the internal memory load module of Freescale's 68HC08 microcontroller can access the internal flash memory after entering the correct eight-byte password. In order to achieve the same time for both the correct and the wrong password, additional free operation instructions have been added to the program. This provides good protection against timing attacks. Some microcontrollers have an internal RC oscillator, so the operating frequency of the processor is related to the voltage and the temperature of the chip. This makes timing analysis difficult, requiring stable component temperatures and reduced noise and voltage fluctuations on the power line. Some smart cards have an internal random clock signal that makes the measurement time delay in the attack invalid.
Third, exhaustive attacks (also known as brute force attacks)
Violence is another meaning for semiconductor hardware and passwords. For passwords, brute force attacks are a large number of keys that the system attempts. It is common to use a high speed computer to find matching keys. An example is the password protection setting in a microcontroller. Take TI's MSP430 as an example. The password itself is 32 bytes (256 bits) long enough to withstand brute force attacks. However, the password is assigned to the same memory address as the processor interrupt vector. Then, first reduce the area that the vector in memory is always pointing to. Then when the software is updated, only a small portion of the password is modified, since most of the interrupt subroutines point to vectors that are the same address.
As a result, if the cracker knows one of the earlier passwords, it is easy to do a systematic search and find the correct password in a reasonable amount of time. Violent attacks can also be implemented in the hardware design of an ASIC or CPLD. In this case, the cracker uses all possible logic combinations to the possible inputs of the component and observes all the outputs. This method is also known as Black-box analysis because the cracker does not know the condition of the component being tested. Try to get the functionality of the component with all possible combinations of signals. This method is very effective for relatively small logic devices. Another problem is that the ASIC or CPLD used by the cracker has a trigger, so the output will probably be the current state or the state of the input. But if the signal is checked and analyzed in advance, the scope of the search can be significantly reduced. For example, clock inputs, data buses, and some control signals are easily recognized.
Another possible brute force attack, effective for many semiconductor chips, is to apply an external high-voltage signal (usually twice the supply voltage) to the chip pins in an attempt to enter factory test or programming mode. In fact, these pins are easy to find with a digital multimeter because they do not have a protection diode to the power supply pin. Once a pin that is sensitive to high voltage is found, the cracker can try a combination of possible logic signals to add to other pins to find the part that is used to enter the factory test or programming mode. The cracker can also use the communication protocol of the component to find out the hidden functions used by the designers to embed the tests and updates embedded in the software.
Chip manufacturers often provide embedded hardware test interfaces for post-testing. If the security of these interfaces is not properly designed, the cracker can easily use it to read and write on-chip memory. In smart cards, these test interfaces are typically located outside of the chip circuit and physically removed after testing. Any security system, regardless of software and hardware, may be flawed in design, an opportunity for crackers, and violent attacks may find it. Careful design of the security system and proper evaluation can avoid many problems and make these attacks ineffective.
Fourth, power analysis (Power analysis)
The power consumption of an computing device depends on its current state. According to the principle of CMOS transistors, the power consumption of each part is larger than that of static. When the input voltage is applied to the inverter, it causes a short circuit in the transistor. The increase in current of this transistor is much larger than the parasitic leakage of static consumption. By adding a 10-20 ohm resistor to the power line, you can measure the current fluctuations. For better results, an analog-to-digital converter with at least 12-bit accuracy and 50MHz sampling speed is required.
These obtained parameters can be used to distinguish different instructions of the processor and estimate the number of bits flipped simultaneously on the bus. By repeating the current of the same operation on average several times, even a small signal that does not pass through the bus can be distinguished. Some signals, such as the shift state, are particularly useful because many cryptographic key generation algorithms use a shift operation to shift out a single key reversal bit flag one by one. Even if the change in status bits cannot be directly measured, they usually change the order of instructions or the execution of the microcode, which can result in significant changes in power consumption.
Different instructions result in different levels of instruction decoding and the activity of the arithmetic unit, which can be clearly distinguished, so that the arithmetic part can be inferred. Different units of the processor have unique switching states at different times associated with the clock edge and can be separated by high frequency instruments.
There are a number of different power analysis techniques used to crack cryptographic algorithms. The entire analysis process is relatively straightforward and requires only standard, inexpensive equipment available. There are two main types of power analysis techniques: SPA (Simple Power Analysis) and Differential Power Analysis (DPA: Difference Power Analysis). The SPA directly observes power consumption during password or other security-related operations, and can learn information such as key data when the device is running. If the cracker knows the cryptographic algorithm, it is easy to find some bits of information by observing the processor instruction order, especially the shift conditional branch. If the results of an algorithm or logic operation are easily seen, such as the carry state, zero or negative flags, more information can be obtained.
DPA is a more efficient technique because the cracker does not need to know how the cryptographic algorithm is executed. It uses static analysis and a large number of power traces of known cryptographic operations to obtain hidden information. Statistical methods are used to identify small differences in power consumption that can be used to recover individual bit information in a key. The power consumption characteristic of course includes the noise portion. Additional noise can be reduced by reducing the length of the probe that acquires the signal and carefully using the measuring instrument. Measuring the power dissipation of a resistor connected to the ground has some advantages. First, the noise level is reduced. Second, the signal can be measured directly with the oscilloscope's probe, as most probe stations have a common ground wire connected to an external power ground. In order to increase the signal to noise ratio, it can be obtained by increasing the average number of samples.
Active probes reduce input capacitance and increase the bandwidth of the input signal. One method is to use a high-speed, low-noise op amp to build a relatively simple probe, and the other is to connect directly to the input of the oscilloscope with a short coaxial cable. In these cases, the input capacitance of the probe is significantly reduced.
The existing power analysis steps have been improved. This is a new approach that has not been similar. We use a core transformer to replace the resistor connected to the power supply or ground, so the waveform is a bit different, because the DC component of the signal is lost, and at the same time there are some advantages. The commonly used method has almost no restrictions on DC current. But for a 10 ohm resistor, a current of 100 mA means a voltage drop of 1 V, which may interrupt the normal operation of the microcontroller.
Reducing this resistance can solve this problem, but it will make it difficult to identify small changes in power consumption. With a transformer, you don't need to use expensive active probes, and standard passive probes give almost the same results. If the signal is too small, adjust the coil on the secondary side to increase the amplitude. The transformer also acts as a passive filter, such as a waveform, and the same processor instructions have different effects on the resistance and the waveform measured by the transformer. That can be done by processing the obtained signal. In order for the attack to succeed, it is necessary to collect thousands of samples and then quickly analyze the secrets presented.
Recently, this type of attack has been considered in chip design and will make this attack method more difficult to succeed.
Five, noise attacks (Glitch attacks)
A noise attack is a process that quickly changes the input to the microcontroller to affect its normal operation. Usually the noise is superimposed on the power supply or on the clock signal, but the noise can also be an applied transient electric field or electromagnetic pulse. By placing two metal pins hundreds of microns from the surface of the chip and then applying a narrow pulse of hundreds of volts less than one microsecond, the wafer substrate induces an electric field that causes the threshold voltage of adjacent transistors to change. An improved method has recently emerged: using a few hundred turns of metal wire around the tip of the microprobe to form a small inductor. When a current enters the coil, a magnetic field is generated and the tip of the needle concentrates the magnetic field lines.
Each transistor and the line connected to it form an RC circuit with a time-delay characteristic. The maximum available clock frequency of the processor depends on the maximum delay of the circuit. Similarly, each flip-flop has a characteristic time window between receiving the input voltage and the resulting output voltage. This window is determined by the given voltage and temperature. If clock noise (much shorter than normal clock pulses) or power supply noise (fast fluctuations in supply voltage) will affect some of the transistors in the chip, causing one or more flip-flops to enter an error state. By changing parameters, the processor is caused to execute many completely different error instructions, sometimes even without being supported by microcode. We don't know in advance which kind of noise will cause any kind of chip error, but it can search the system quite simply.
1, clock noise attack (Clock glitches)
The noise attack of the clock signal is currently the simplest and quite practical. Noise in practical applications is often used to replace jump conditions and test previous test instructions. An attack window can be created during secure password challenge processing to simply prevent these instructions from being executed. Command noise can also be used to increase the cycle time. For example, the serial port subroutine reads more content after the output buffer; or reduces the number of loops during the key operation to pass a weak password. To get noise, the clock needs to be temporarily increased by one or more than half a cycle, and some triggers get input before they reach the new state. Clock noise is typically directed to the processor's instruction stream. Microcontrollers that perform hardware security on the hardware have no effect. In practice, only the clock noise is used to attack the software program interface of the microcontroller or smart card.
The cracking of such protection is relatively easy. If the processor executes only one instruction in the loop, different clock noises can be used during the attack to cause the processor to malfunction. You don't need to be careful with the clock signal, you only need to randomly make noise to be successful in several attacks. Inserting noise is relatively easy, and you don't need to use an external generator to short-circuit the crystal. When the resonator oscillates on different overtones, it will emit a lot of noise. In most cases it is necessary to obtain the desired result within a certain clock cycle, in which case it is better to use a signal generator.
Using clock noise to attack some microcontrollers can be difficult. For example, the instrument module of the German MPS430 microcontroller operates in the internal RC oscillator. It is difficult to synchronize with the internal clock, and it is difficult to estimate the exact time when attacking. Some smart cards randomly insert delays into the processor instruction stream, making the attack more difficult. Using power analysis can help, but requires very expensive equipment to get the reference signal in real time.
2, power noise attack (Power glitches)
Fluctuations in the power supply voltage can cause drift in the transistor threshold level. The result is that some flip-flops sample their inputs at different times or read the status of the wrong safety fuse. Noise is usually generated by instantaneously increasing the supply voltage or voltage drop, typically within 10 clock cycles. Power supply noise is typically used on the microcontroller's program interface to affect processor operation or hardware safety circuitry. In general, weak points are more difficult to find and exploit than clock noise because for time domain parameters, amplitude, rise/fall times are variables.
An example is the attack MC68C05B6 mentioned in the previous example. If the power supply voltage is reduced by 50-70% when the AND $0100 instruction is executed, the value fetched by the processor from the EEPROM is FFh instead of the actual value. This will correspond to the unencrypted state of the fuse. The trick is to carefully calculate the execution time to reduce the supply voltage, otherwise the processor will stop running or enter a reset state. This task is not difficult, the target instruction is executed in the first hundred cycles after reset. Crackers can use vector generators or build their own noise sources.
The other is the old PIC16F84 with a micro core. The erase operation of the chip will release the security protection. But at the same time, the contents of the program and data memory on the chip. The safety protection circuit is designed to erase the memory before the safety fuse is reset. However, we have found that increasing the power supply voltage to about 10V in a few microseconds during a chip erase operation interrupts the memory erase operation, but the safety fuse normally completes the reset, which makes it possible to read the contents of the memory. Such high voltages need to be used with caution, and if the time is too long, the chip will be damaged. The new version of the PIC16F84A adds protection against undervoltage and overvoltage attacks. If the supply voltage is lower than 3V or 6V, any modification of the memory through the programming interface will be interrupted immediately.
Specifications that do not always require power supply noise to exceed the supply voltage range. For example, with the PIC18F84A microcontroller, the protection mechanism prevents noise greater than 50mV from being used after the chip erase operation begins. That would result in the abort of the program memory erase operation but will not erase the fuse.
The above example shows that noise attacks can be very effective without special tools. There are clock monitoring circuits in the smart card but very few microcontrollers.
Sixth, data retention capability analysis (Data remanence)
The processor will generally store the key in static RAM. If the component is tampered with, it will be powered down and the RAM content will be lost, thus protecting the key from being stolen. It is well known that the content in the SRAM will "freeze" below 20 degrees below zero. Many components consider the temperature below this threshold to be considered a tamper event. We did some experiments to determine the relationship between modern SRAM data retention and temperature. Our experiments show that traditional thinking is no longer effective. Data retention is a problem even at high temperatures. Data retention capabilities not only have an impact on SRAM, but also on DRAM, UV EPROM, EEPROM and flash memory. As a result, some information can still be obtained from the erased memory.
This can cause a lot of problems for security devices. Security engineers are concerned about the time that SRAM devices can hold data after a power outage. The reasons are as follows: Many products use encryption or similar methods for encryption and other security-related calculations that need to be unreadable or changed. The most common solution is to place the security key in a volatile memory with a tamper sensor. Once tampering is detected, the volatile sensor will be powered down or shorted to ground. But if the data retention time is greater than the time the cracker opened the component and powers up the memory, the protection mechanism is destroyed.
In the 1980s, low temperatures were found to increase the data retention time of SRAM to seconds or even minutes. For the components at that time, it is found that minus 20 degrees can increase the data retention time, and will increase the retention time as the temperature decreases. Some have added a temperature sensor that triggers a tampering event when the temperature is below minus 20 degrees and immediately clears the memory. This test is repeated to see if the product after 2000 has this characteristic.
Another concern is that even if part of the content has been destroyed, the security information can be restored. Suppose the cracker obtains m=115 bits in the n=128-bit key, which is 90% of the information. He can search for n! /(m!(nm)!=128!/(115!13!)=2.12*1017~258 possible keys. Through 10,000 computers, each operation is performed with 1 billion search keys per second. It takes only 6 hours for the cracker to search through all the keys. If there is only 80% of the information, that is, 103 of the 128-bit keys, there are 2.51*1026~288 possibilities. Almost one increase. A hundred times, the cracker has to spend millions of years searching for keys, so it is considered that a uniform 128-bit key cannot be recovered.
Pmic Energy Metering,Pmic Ic Energy Meter,Electronic Components Pmic Energy Meter,Circuit Pmic Energy Metering
Shenzhen Kaixuanye Technology Co., Ltd. , https://www.iconlinekxys.com
