Pulling cable is the last resort to prevent cyber attacks.

Introduction: Pulling cable is the ultimate move to prevent cyber attacks. You guys, design.
In 2014, SONY was hacked by North Korea and all confidential information was swept away. The legend is that employees pulled out the network cable at the last moment and managed to keep the "underwear." This "drawing cable" approach seems to cure all diseases. However, as long as the broken network can guarantee the information on a computer to sit back and relax? (Of course it isn't, or wouldn't it be written in the end?)
For a long time, there are three ways to get a key on a computer:
1. Get this computer directly and then enter the Trojan virus to steal it. (The risk of this slightly LowB method is that if the computer owner "sniffs on the bed" and angers the police, then the hackers need to have certain escape skills).
2. Invade the target computer through the Internet, install Trojans remotely and steal keys. (Most hackers use this method while ensuring their own forcing and personal safety)
3. If the target computer is not connected to the Internet, the virus should be ferried to the target computer through a medium (such as a USB flash drive) that can contact the Internet. (This method has high technical difficulty because of the forced grid fullness. Only a few successful cases such as the U.S. attack on Iranian nuclear power plant have been visually observed.)
Now these methods are weakly exploding.
An Israeli white hat hacker (security researcher) has developed a high-energy game that requires only a large "stethoscope" next to yours to capture your password information based on the electromagnetic waves emitted while your computer is working. .

â–²Can hear the computer "talk to himself" electromagnetic wave detector
The counterattack of this attack method lies in:
1, the speed is very fast, only a few seconds, the key to hand.
2. It does not involve password cracking at all, but captures the plaintext of the password directly. The so-called partition wall has ears and probes.
3, no computer networking, no need to contact the "victim computer." No strokes were found. The outcome was judged.
To make this device, it only costs 3,000 US dollars. It can accurately capture the electromagnetic waves around the computer while it is working, and it can be amplified and analyzed.
So, what exactly can this "eave device" hear?

â–² Monitored computer
The researcher tried to send an encrypted email to the victim computer. During the process of opening the e-mail on the computer, the decryption operation was performed in the background. And it was this decryption process of just a few seconds that the emitted electromagnetic waves carried the “secret of the universeâ€. After analyzing the electromagnetic waves for a few seconds, the eavesdropper discovered that each time a narrow-band signal appeared, it marked the decryption of a password. After parsing these narrow-band signals together, the ciphertext information flows so easily.
The researchers passed through 15 cm thick walls and captured 66 decryptions. It took only 3.3 seconds to get the key.
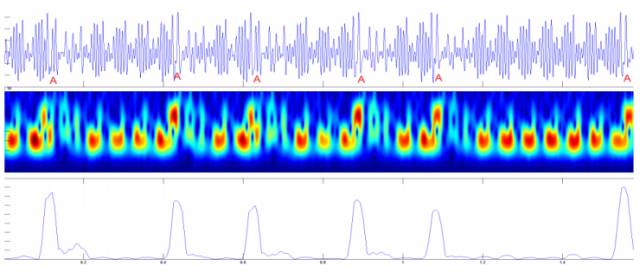
â–² fluctuations in electromagnetic waves, marked at the narrow-band signal
This experiment is tantamount to discovering the "gravitational waves" of the hackers and opening up new holes for hackers. This signifies that the computer will talk to itself when working. As long as you can understand what the computer is saying, then this computer will have no secret in front of you. With the same principle, it is even possible to analyze other information generated during computer work, such as bank card passwords and private chat contents.
Researcher Tromer said: "This type of attack is likely to quickly go out of the lab and become a popular method of attack. Hackers will study cheaper equipment and further reduce the cost of attack." However, if the hackers want to make This kind of equipment needs to overcome a big obstacle that is to filter out the background noise. Analysing the innumerable electromagnetic waves that are produced by computer work is like hearing a girl whispering on a noisy Party. Achieving such a posture requires a very strong physics foundation, and it is not a traditional dead-house procedure that can be done.
If this type of attack becomes a "standard" for hackers in the future, it is really a matter of trepidation. Traditional offensive measures need to pass through the Internet. Hackers can easily leave traces on your computer. These traces can be used as evidence for them. Electromagnetic waves are eavesdropping on people, but there is no means to detect them. So you want to know It is almost impossible to be "listened" to yourself.
Just as Tromer said:
Our computers are heavily protected in the online world, but they are almost naked in the physical world.
When you are still tangling with a mosaic, hackers have already seen your skin and bones. In the face of this reduction in dimension, the privacy of each of us is even more fragile. Even to the point where people do not know, unless they are not.
After careful thinking, in order to prevent information from being hacked, the correct use of the computer is as follows:

Cbd Vape Products Oem,D8 Vape Pen Oem,Cbd Disposable Vape Pen Oem,China Cbd Vape Products Oem
Shenzhen MASON VAP Technology Co., Ltd. , https://www.disposablevapepenfactory.com
